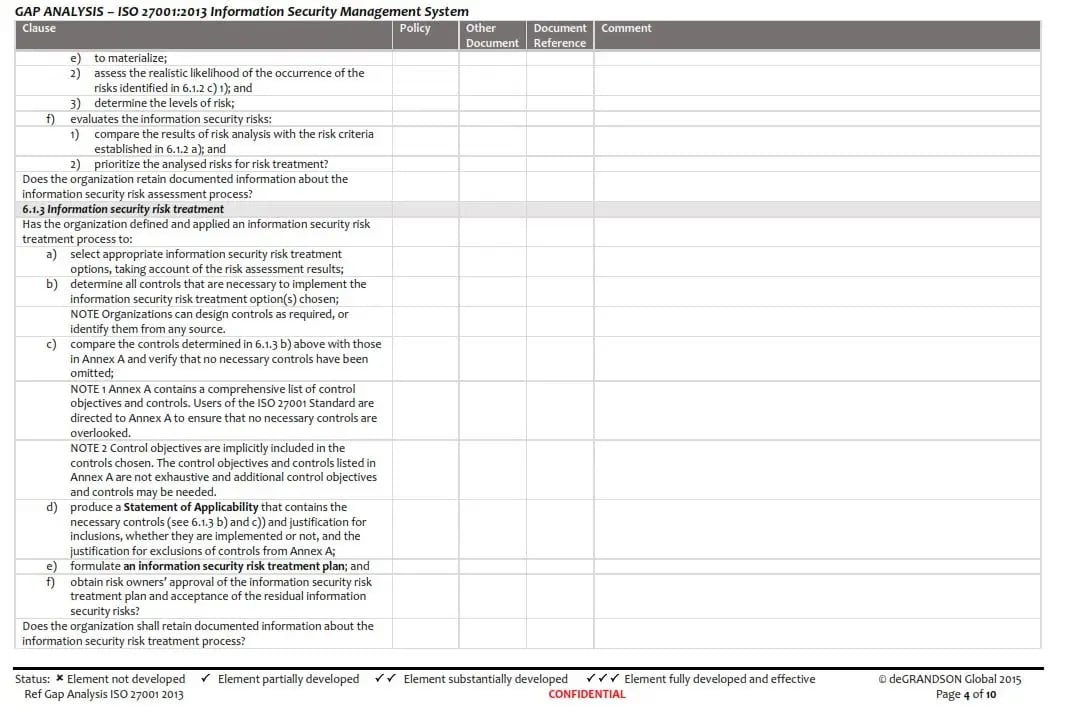
Demonstrating compliance with Annex A requirements of Annex A to your Certification Body
Using ISO 27001 controls outlined in Annex A alone to address security vulnerabilities is never enough!
What is ISO 27001 Annex A about?
Let's begin with ISO 27001 Annex A. Annex A controls aim to ensure that a comprehensive set of controls is in place to manage information security risks. We emphasize this in all our ISO 27001 training courses because applying these Controls is fundamental to complying with the Standard's requirements.
As the vulnerabilities and threats to information security vary from one organization to another, the vulnerabilities included in Annex A should be treated as a 'fallback' position.
External auditors will not be satisfied with information security controls that address Annex A vulnerabilities alone. Without additional vulnerabilities particular to your organization (and consideration having been taken of the several sectoral Codes of Practice that may apply, e.g., ISO 27018 regarding personally identifiable information, external auditors will likely believe that no authentic risk assessment was done.
This may give them the impression that you've gone through the motions of preparing information security management system (ISMS) documentation to provide the appearance of meeting requirements.
In this circumstance, you've little chance of being recommended for Certification to ISO 27001.
How to Provide Evidence to Prove ISO 27001 Annex A Compliance
The external auditors will look for multiple pieces of evidence of effective implementation of controls and precautions related to applicable ISO 27001 Annex A vulnerabilities. They would also look for other vulnerabilities specific to and identified by the organization.
Here are some examples of ways you can prove compliance with ISO 27001 Annex A:

1. Direct Observation
This is the best quality of audit evidence. Verifying and recording in the Audit Workbook that:
- a locked door is locked,
- people do sign confidentiality agreements,
- the asset register exists and contains assets observed,
- system settings are adequate, etc.).
2. Keep Records of Performance
Evidence can be gathered from seeing the results of the performance of a Control. Having sight of and recording in Audit Workbook:
- printouts of access rights given to people signed by the correct authorizing official,
- records of incident resolution,
- processing authorities signed by the correct authorizing official,
- minutes of management (or other) meetings.
3. Perform Direct Testing
Evidence can result from the auditor's direct testing (or re-performance) of controls. For example:
- attempts to perform tasks said to be prohibited by the controls,
- determination whether software to protect against malicious code is installed and up-to-date on machines,
- access rights granted (with the permission of management/authorities).
4. Conduct Interviews
This is arguably the most crucial form of evidence. Many organizations operate on the basis that if IT vulnerabilities are controlled, the organization is protected. This is folly. We're not talking about cyber security—it's more than that—we're talking about information security!
We know that all the technological precautions in the world are essentially useless unless the people involved fully play their part. People are always the weakest link in the chain; just read about significant information security breaches, and you will see that time after time, the failure of the people involved (actively or passively) permitted the incident to occur.
Interview persons doing work under the organization's control about applicable processes (especially outsourced processes) and controls, then determine whether this is factually correct. Confirm the evidence by interviewing contractors and sub-contractors (both management and staff) about applicable processes and content.
How Annex A of ISO 27001 Affects Your Internal Audit Programme
Too often, Audit Programmes for organizations seeking certification to ISO 27001 ignore Annex A or schedule a cursory audit of the requirements here.
Remember, Annex A is not 'Informative' but 'Normative'—that is, it is a mandatory part of the Standard.
It is essential that a sufficient number of internal audits be planned to cover all applicable vulnerabilities (upward of a hundred are common) and evidence of the types given above to be collected and documented. Otherwise, you have little chance of a successful Certification . Good luck.
Select the best ISO 27001 Course.
We have five ISO 27001 Courses, including Extension and Conversion Courses. See our ISO 27001 course overview page to see the full range of options.
Related Courses
Related Courses
Related Articles
- How does ISO 27001:2022 Compare with ISO 27001:2013?
- Free ISO 27001 Implementation Handbook (100+ pages)
- Navigating the fifty-six ISO 27000 Series of Standards
- Information Security Standards other than ISO 27001
deGRANDSON Global is an ISO Certified Educational Organization
In October 2021, we secured certification to three education-related ISO Standards. We now have a university-grade management system that conforms to the requirements of …
October 2021, we secured certification to three education-related ISO Standards. We now have a university-grade management system that conforms to the requirements of …
We have chosen ISO 21001 certification because it is based on independent third-party assessment, unlike IRCA and Exemplar badges (which we believe are commercially compromised). It is a 'university grade' standard used globally by schools, colleges, and universities to demonstrate competence.
We offer Courses for ISO 9001, ISO 13485, ISO 14001, ISO 17025, ISO 27001, ISO 45001, Data Protection, Risk Management, and more.
Written by Dr John FitzGerald
Related Articles…
QMSR & ISO 13485: On 02-Feb-26, the FDA Final Rule comes into force. The amendments incorporate by reference (and so align more closely with) the international standard ISO 13485:2016, Medical Devices - Quality Management Systems - Requirements for regulatory purposes. Did you know that cybersecurity is addressed in ISO 13485:2016, ... Continue reading
Securing certification to this Information Security standard requires a collective effort. Implementing ISO 27001, the international standard for Information Security Management Systems (ISMS), can be complex, and several common errors may need to be corrected during the implementation process. Frequently Encountered Errors when ... Continue reading