Recommended as part of ISO 27001 Training or on Day 1 of Induction Training for new recruits
A cyberattack can destroy a business. Whether that involves Denial-of-Service, deletion of files, ransomware, or other types of cyberattacks, the most frequent event they all have in common is human failure. Currently, the most common human failure is becoming a victim of a Phishing e-mail, which has been attributed to >90% of successful information security breaches.
You may be surprised to learn that the most likely target organizations are smaller organizations that are likely to be suppliers to major organizations. The smaller organization is perceived as an easier route to successfully attacking the major one.
From the moment anyone has access to a company PC, Laptop or another device capable of receiving and sending email, you are vulnerable to Phishing. And phishing emails are not always easy to spot Action is needed by you. And so, this short video presentation, which is free, is recommended as part of Day-1 Induction Training for new Recruits and as a refresher course.
Why is Information Security Training Necessary?
Published research shows that the human factor is the 'weak link' in cybersecurity. Yet, despite this knowledge, the situation is not improving. Our own experience in on-site auditing confirms this. People working for companies seeking ISO 27001 Certification are simply not vigilant about maintaining the organization's information security.
And no more so than their lack of awareness of the dangers of spear phishing and their helplessness in the face of clone phishing. The fact that snippets of sensitive information from various sources within an organization can be spliced together to facilitate a crushing cyber attack simply does not register.
Costliest Phishing Attacks in Recent History * |
||||
| Phishing Victim | Industry | Year | Estimated Losses | Mode of Attack |
| Sony Pictures | Entertainment | 2014 | $100 million | Spear Phishing |
| Facebook and Google | Technology | 2013-2015 | $100 million (combined) | CEO Fraud |
| Crelan Bank | Banking | 2016 | $75.8 million | CEO Fraud |
| FACC AG | Aerospace | 2016 | $47 million | CEO Fraud |
| Ubiquiti Networks | Technology | 2015 | $46.7 million | CEO Fraud |
| Leoni AG | Energy and Data Management | 2016 | $44.7 million | CEO Fraud |
| Xoom | Money Transfer | 2014 | $30.8 million | CEO Fraud |
| Pathé | Entertainment | 2018 | $21 million approximate | CEO Fraud |
| Tecnimont SpA | Engineering, Technology, Energy | 2019 | $18.45 million | CEO Fraud |
| The Scoular Company | Farming | 2015 | $17 million | CEO Fraud |
* That we know of. Data retrieved March 04, 2022
Common Problems with Information Security Training
In most security breaches, there are training records to inform us that cybersecurity training has taken place, but there are two repeated problems. Firstly, the training is rarely given as part of induction training, when recruits are most likely to compromise information security arrangements inadvertently, and, secondly, the adequacy of the awareness training is rarely evaluated (such evaluation itself acting to reinforce awareness). To address the problem, we have produced a 9-minute video presentation called 'The dangers of Phishing'. If you like the video, feel free to use it as part of your Induction Training. Just add a link to it in one of your own Induction Training presentations.Afterwards, we recommend that you evaluate the effectiveness of the training given for Cyber Security Awareness. Periodically circulating a test phishing email and subsequent review of outcomes with all concerned is especially effective in engendering continuous vigilance. We also suggest including short interviews of all staff as part of your Internal Audit Programme for your Information Security Management System.
Interested in ISO 27001, the Information Security Management System Standard?
If so, we have a selection of auditor and implementer training courses that might be relevant to you. Please click on the button below to learn more about them.
If you have any questions, you can refer to our ISO 27001 course overview page, where you can see some of our answers to frequently asked questions, or contact us. We're always delighted to help.
Related Courses
Related Courses
Related Articles
- ISO 27001 in Manufacturing and Service Industries - 18 FAQs Answered
- Information Security Standards other than ISO 27001
- Integrating Cyber Security in Medical Device Management
deGRANDSON Global is an ISO Certified Educational Organization
 In October 2021, we secured certification to three education-related ISO Standards. We now have a university-grade management system in place conforming to the requirements of…
In October 2021, we secured certification to three education-related ISO Standards. We now have a university-grade management system in place conforming to the requirements of…
We have chosen ISO 21001 certification because it is based on independent third-party assessment, unlike IRCA and Exemplar badges (which we believe are commercially compromised). It is a 'university grade' standard globally by schools, colleges, and universities to demonstrate competence.
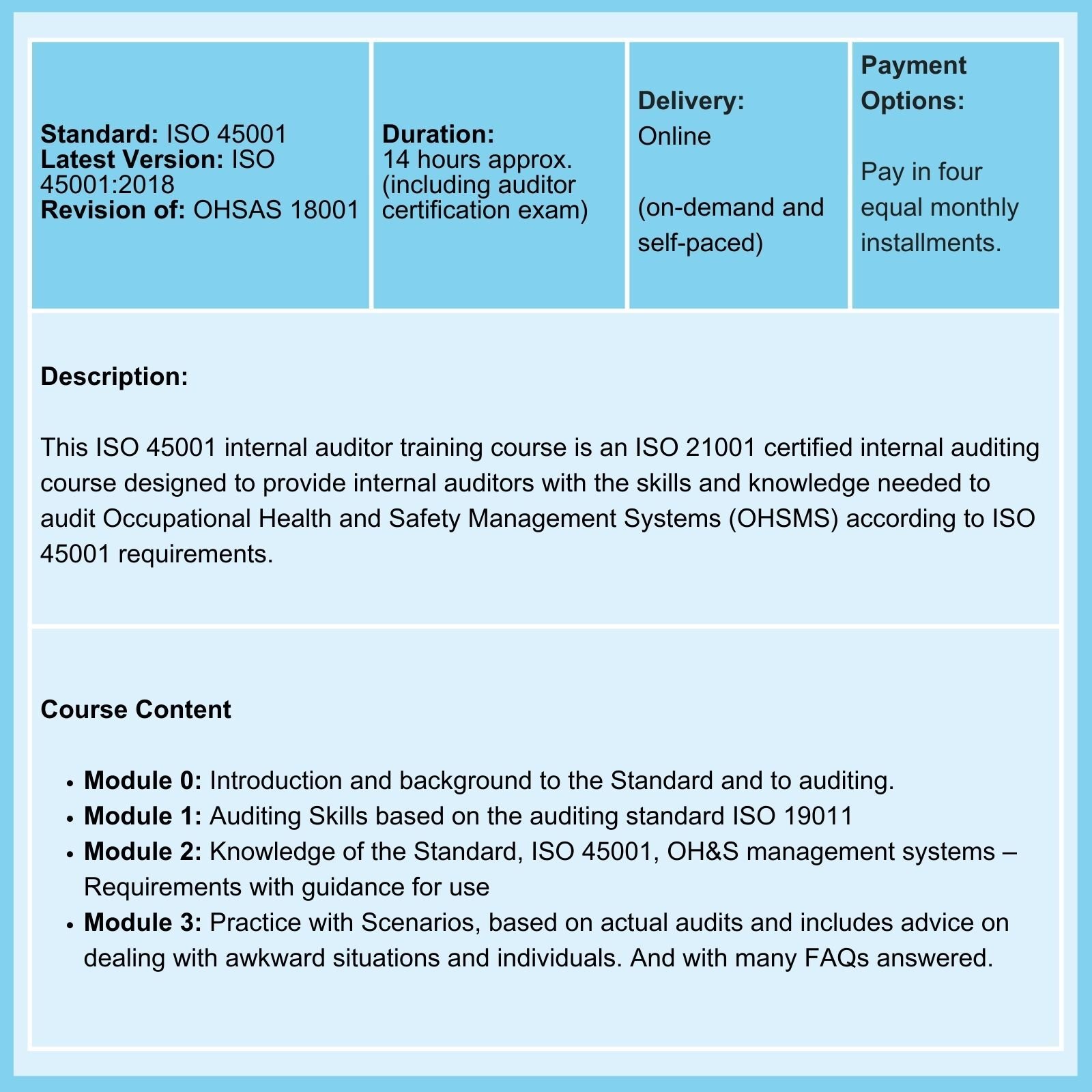
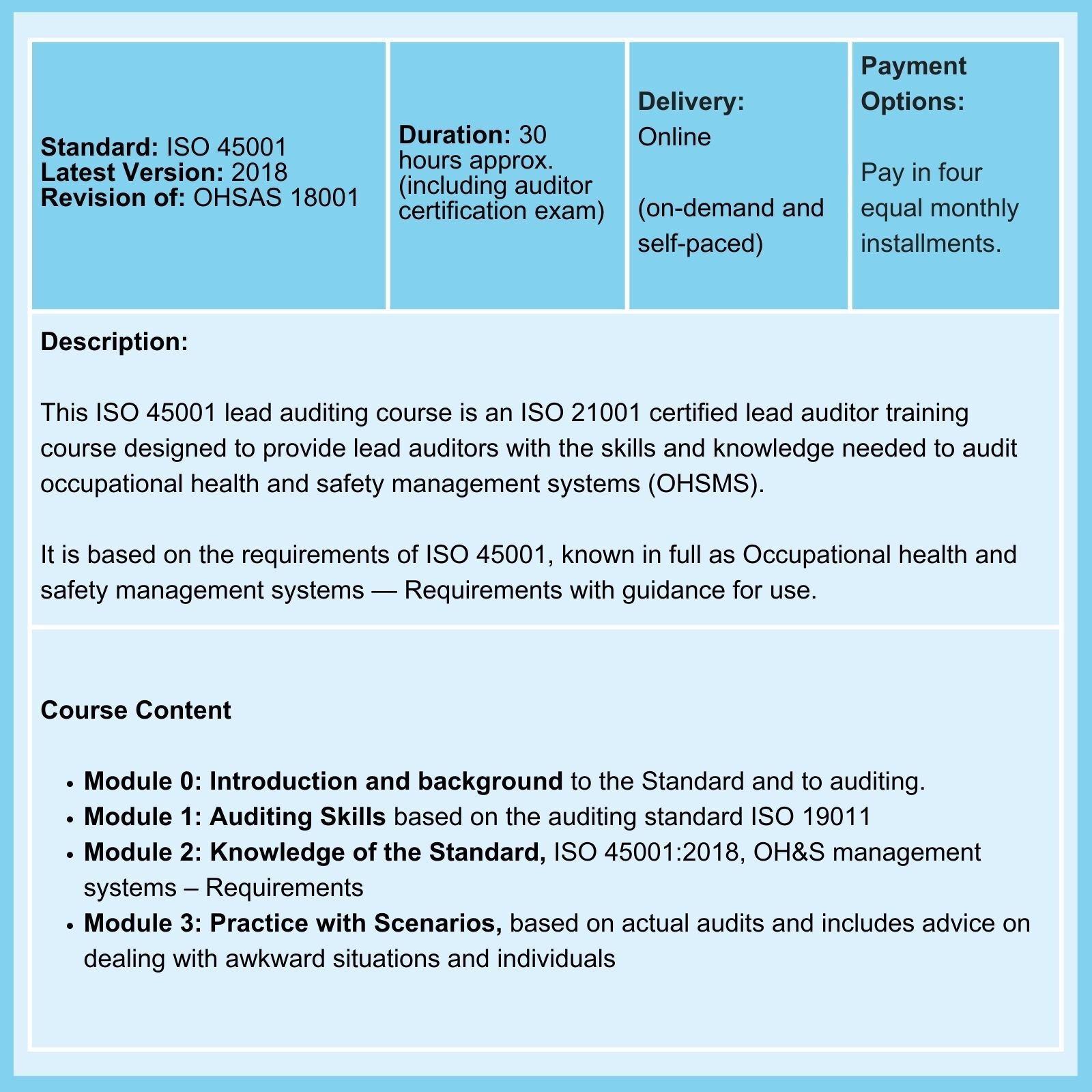
We provide Courses on ISO 9001, ISO 13485, ISO 14001, ISO 17025, ISO 27001, ISO 45001, Data Protection, Risk Management, and more.