The fourth edition of this Standard was published in October 2022, but it's rarely referenced in ISMS documentation.
What You Need to Know About ISO 27005
What is ISO 27005 for?
ISO 27005 provides the framework for managing risk so that you can customize your methods to suit your individual needs.
ISO 27001 vs ISO 27005
ISO 27001 is intended to be applied to all types of organisations, and there is no 'one size fits all' approach upon which to depend. You need to use a specific approach to each economic sector to achieve maximum benefit.
The involvement of your (proposed) Information Security Team in developing an information risk management framework (as guided by ISO 27005) from the outset is a great way to get buy-in and commitment to your ISO 27001 Project. Don't ignore this Standard, please.
Who Should Study the ISO 27005 Standard?
ISO 27005 (also known as IEC 27005) will be, or should be, of particular interest to:
- IT Managers and those who implement and maintain an ISMS for their organisation,
- Consultants and Advisers who develop, implement and maintain ISMSs, and
- Lead Auditors who wish for a deeper understanding of how risk should be addressed in an ISMS.
Those expecting to find techniques and methods for managing risk will be disappointed as ISO 27005 focuses on the issues and the thinking that should precede the selection of risk management tools and methods (you'll find that in our ISO 27001 training). The best choice for risk management tools and methods remains IEC 31010:2019 Risk Management - Risk assessment techniques. With 40+ useful tools explained with examples, this is the 'Gold Standard' for risk management.
ISO 27005:2018 Clauses
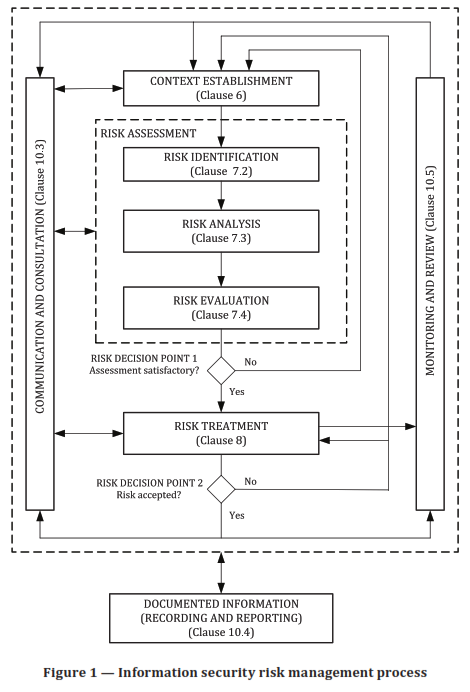
This standard focuses on the information security risk management process and the information security risk management cycles. You are taken step by step through the process following the process map shown here, which is taken from the standard.
And as is often the case in ISO Standards, the best has been kept 'til last - the Annexes.
ISO 27005 Annex A
This Annex titled Examples of techniques in support of the risk assessment process is a 'goldmine' of practical information. Subjects covered here include...
- Criteria related to risk criteria ( a widely misunderstood topic)
- Risk acceptance criteria
- Information security risk components
- Assets
- Risk Sources and desired end states
- Event-based approach
- Asset-based approach
- Examples of scenarios applicable in both approaches
- Monitoring risk-related events
Throughout, copious examples are given which are the true value of this Standard. Even the vexed question of 'Vulnerability' versus 'Threat' is clearly explained in simple English. This Standard is essential for those professionally interested in ISO 27001 and all things about Information Security, and this Standard is essential reading.
ISO 27005 Resources
For more information and to buy a copy of the new Standard, go to the ISO Website.
A good source of information on all things to do with ISO 27001 is iso27001security.com.
Related Articles
- 10 Simple Cyber Security Tips for SMEs
- Information Security Standards other than ISO 27001
- Risk Management in ISO Management System Standards
deGRANDSON Global is an ISO Certified Educational Organization
In In October 2021, we secured certification to three education-related ISO Standards. We now have a university-grade management system in place conforming to the requirements of …
We have chosen ISO 21001 certification because it is based on independent third-party assessment, unlike IRCA and Exemplar badges (which we believe are commercially compromised). It is a ‘university grade’ standard globally by schools, colleges, and universities to demonstrate competence.